VMFS Recovery: restore data from Infected VMDK Files
Typical Virus Attack purpose:
Ransomware
Ransomware is designed to lock or encrypt files on a system, rendering them inaccessible until a ransom is paid. The goal is financial gain, often forcing victims to choose between paying for decryption keys or losing their data.
Data Destruction
Some viruses aim to corrupt data by overwriting it with junk or other destructive content. These attacks are intended to cause irreversible damage, making data recovery difficult or impossible without proper backups.
Virus Tactics:
Attackers often choose between maximizing damage or maximizing the spread of infection. Many viruses take a hybrid approach by encrypting or overwriting only parts of the affected files. This allows the virus to operate more quickly, disrupt services, and leave files unusable, requiring immediate recovery. However, this partial encryption or corruption can still be devastating, as critical parts of the files become inaccessible.
In ransomware scenarios, files remain locked until a ransom is paid to obtain the decryption key. In other cases, recovery may be possible through backups or specialized recovery tools. Unfortunately, data that has been overwritten or fully encrypted cannot be restored. The success of recovery efforts depends on the extent of the damage and the type of data affected.
Methods of Recovery:
When dealing with infected or corrupted VMDK files (used by virtual machines), partial data recovery is often possible. VMDK files are robust and can withstand significant damage, particularly since they often contain both operating system and application-level data. These components are relatively easy to replace.
For example, if a VMDK file contains a Linux virtual machine providing database services, and you can extract the database files, you can quickly create a new virtual machine with a fresh OS and application stack, ready to deploy the recovered database files. This process can typically be completed within an hour, minimizing downtime.
Step-by-Step Guide for VMDK Data Recovery:
VMFS Recovery works with many VM formats and disk images. This article covers the VMDK files but recovering data from simple disk images like DSK, IMG, BIN, virtual machine disks like VHD\VHDx, VDI, HDS, QCOW2\QCOW2c, EnCase, and ProDiscover forensic images are all the same.
Backup: Before beginning the recovery process, create a disk image or forensic image of the disk to preserve the original state. Always make a backup copy of the corrupted VMDK file.
Mount the VMDK in VMFS Recovery: From the main menu, go to Drives -> Mount Disk and follow the wizard.
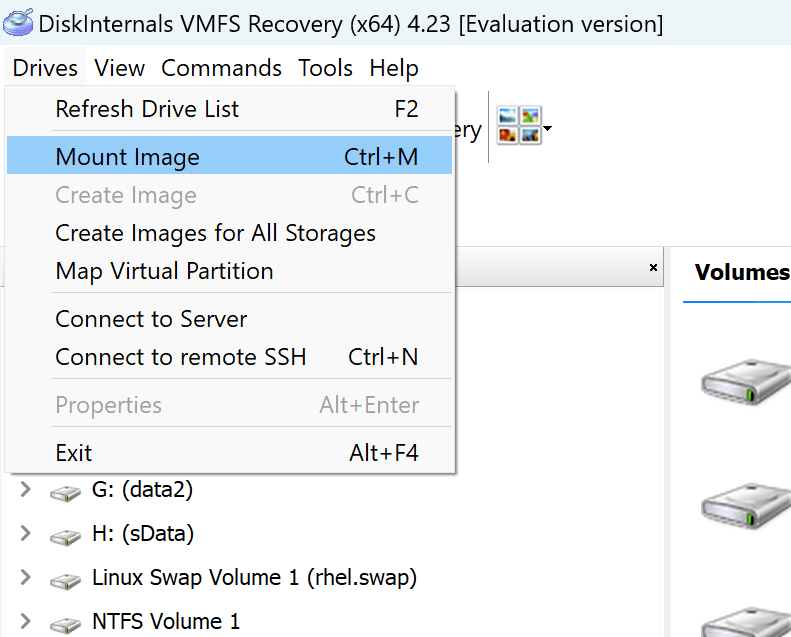
Locate the Partition: After mounting, look for the partition from the VMDK in the "Volumes" section of the disk list. It should approximately match the size of the VMDK and display the correct guest file system.
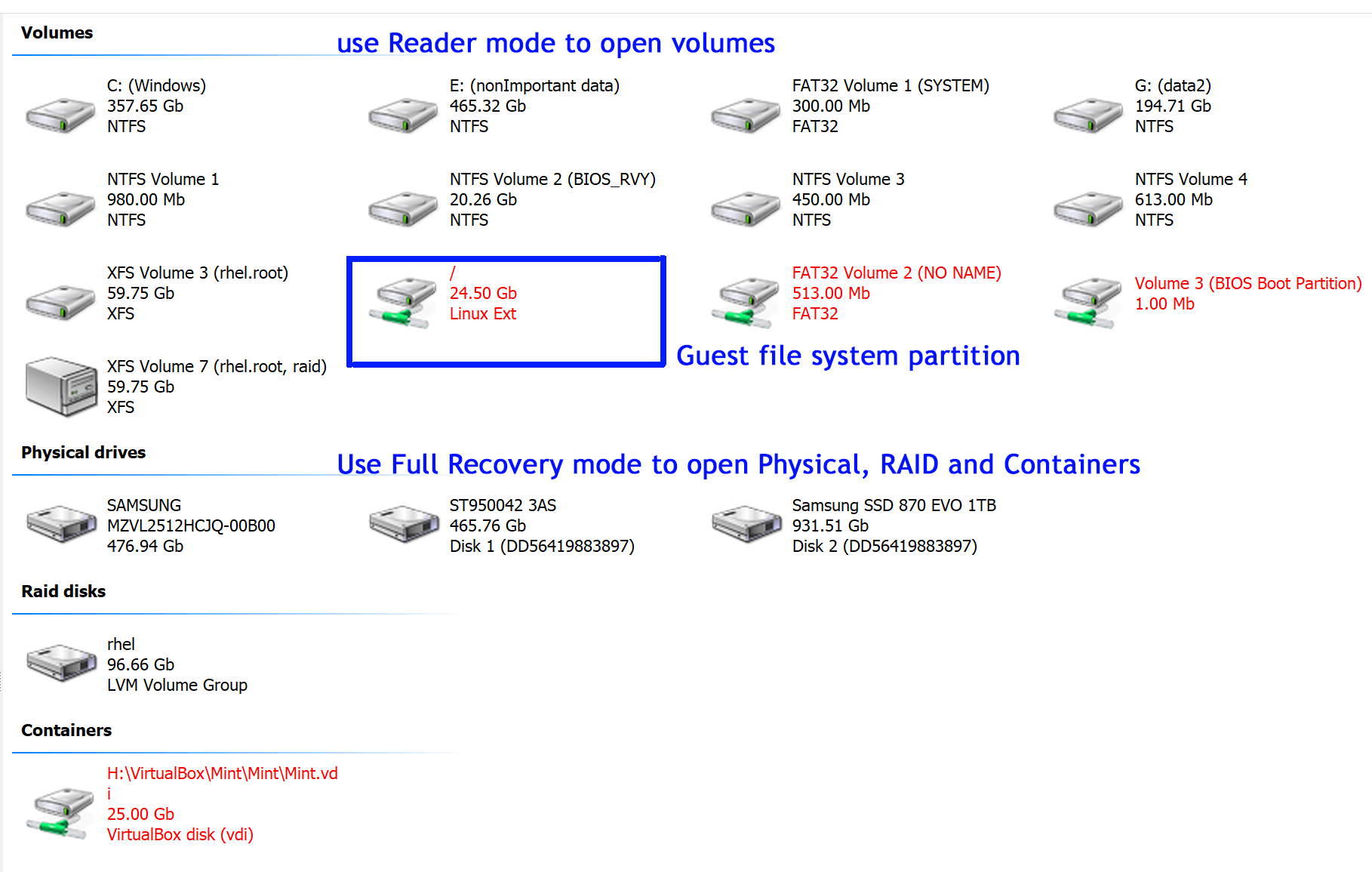
Open the Partition: Double-click on the partition to open it. Select "Reader" mode first and if it fails to display correct data on the built-in preveiw proceed to "Full Recovery - FS," where "FS" corresponds to the guest file system (e.g., ext4 for Linux).
Handle Missing Partitions: If the partition isn't detected, open the mounted disk image in RAW mode and select "Full Recovery - FS" corresponding to the guest file system.
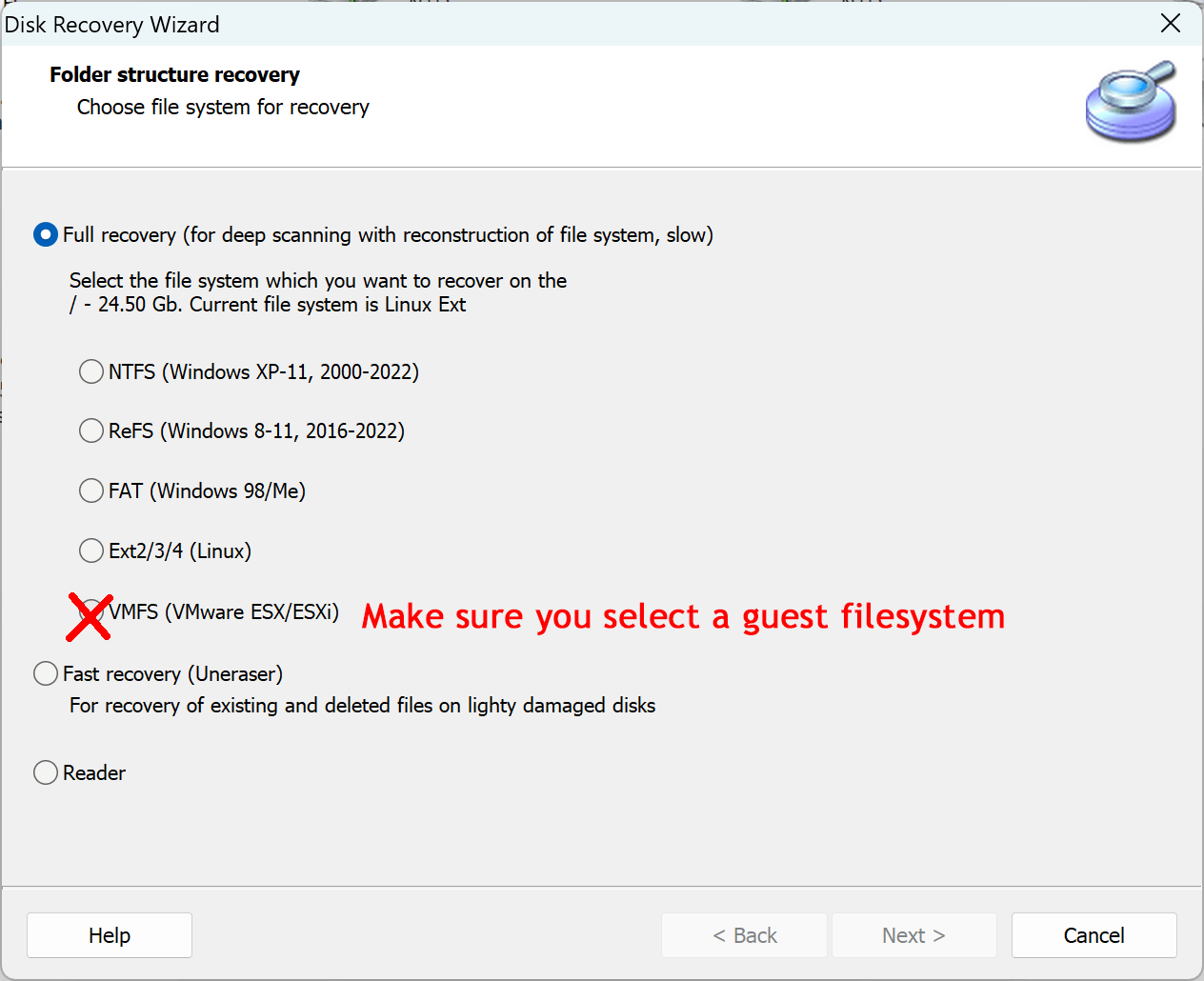
Scan and Review Files: Wait for the scan to complete, browse the recovered files, and use the built-in preview to check file integrity before finalizing the recovery.
What We Cannot Do:
Virus Removal: Our products cannot remove viruses from infected VMDK files. However, you can extract clean data files and deploy them to a new VMDK environment.
Decryption: VMFS Recovery cannot decrypt encrypted files. If ransomware has encrypted portions of a file, recovery is only possible for unencrypted parts.
On-fly fixes: Our company policy is Non-Intrusive Recovery. We do not modify original files or disks. Our software is designed to save recovered data to a third-party disk, ensuring no changes are made to the infected disk’s state.
Hints for Safe Recovery:
To minimize the risk of infecting the recovery environment:
Use a Dedicated VM: Perform recovery operations in an isolated virtual machine. Limit the VM’s network access with a firewall and ensure the environment is protected by up-to-date antivirus software. The internet connection for this VM should be disabled—it isn’t required for VMFS Recovery activation or for the recovery process, and this will prevent the virus from spreading.
Clean OS Install: If you choose not to use a VM, boot from a clean, offline recovery environment (e.g., a live USB with a clean OS) to avoid activating any malware while scanning or extracting data. This is particularly useful against fileless malware or rootkits. However, be aware that some environments like WinPE are limited to 48 hours of runtime, which may not be sufficient for larger recoveries. Rebooting the OS will restart the recovery process, and limited network support may prevent saving recovered data to network disks.
Run Antivirus Scans: Always scan recovered data with antivirus software before redeploying it, even if the files appear clean.
Limit Recovery to Data Files: Focus on recovering data files (e.g., databases, documents) rather than executables. Viruses rarely infect non-executable files, as these cannot execute malicious code on their own.
Handle Scripted Files with Care: Files containing embedded scripts (e.g., Microsoft Office documents, HTML pages, PDFs) should be treated with caution. Run them through antivirus scans before redeployment to prevent any malicious code from being executed.
Avoid Executables: Do not run any executable files, including DLLs, from the infected system. Even documents that support scripting languages (e.g., .doc, .docx, HTML files) may pose risks. Stick to safer formats like .txt or .rtf for opening documents during the recovery process.